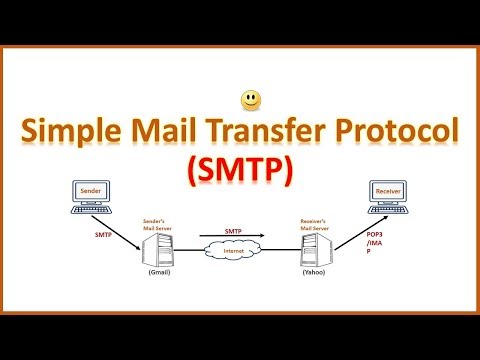
THE SMTP PROTOCOL
 If email is email, SMTP is the postman. Without the standard network protocol of the modern Internet it would not have been possible to send application documents, videos, mp3s etc. This is because when you send an email, it doesn’t go directly to the recipient, but instead goes through a complex process of communicating with numerous instances before arriving at its destination. The SMTP server is a mail server that sends e-mails from a sender to one or more recipients on the Internet and forwards them over the network according to the rules of the SMTP network protocol. An important function of the SMTP server is to avoid spam through authentication mechanisms thanks to which it is possible to send e-mails only to authorized users. For this purpose, most modern e-mail servers support the ESMTP protocol extension with SMTP authentication. Like so-called relays, SMTP servers are the essential link for e-mail transmission, in which several servers are involved: the sender’s outgoing mail server, one or more external relay servers and the incoming mail server of the recipient.
If email is email, SMTP is the postman. Without the standard network protocol of the modern Internet it would not have been possible to send application documents, videos, mp3s etc. This is because when you send an email, it doesn’t go directly to the recipient, but instead goes through a complex process of communicating with numerous instances before arriving at its destination. The SMTP server is a mail server that sends e-mails from a sender to one or more recipients on the Internet and forwards them over the network according to the rules of the SMTP network protocol. An important function of the SMTP server is to avoid spam through authentication mechanisms thanks to which it is possible to send e-mails only to authorized users. For this purpose, most modern e-mail servers support the ESMTP protocol extension with SMTP authentication. Like so-called relays, SMTP servers are the essential link for e-mail transmission, in which several servers are involved: the sender’s outgoing mail server, one or more external relay servers and the incoming mail server of the recipient.
SENDER’S OUTBOUND MAIL SERVER
After the sender has sent his e-mail, the web mail application of his provider or his mail program (the SMTP client, also called “Mail User Agent” or abbreviated to MUA) converts it into a header and a body and uploads both to the outgoing mail server, then an SMTP server.This server has a so-called “Mail Transfer Agent” (MTA), the software base for sending and receiving e-mails. The MTA checks the size of the mail and spam and then saves. To lighten the load on the MTA, a “Mail Submission Agent” (MSA) is occasionally pre-installed, which preliminarily checks the validity of the mail. The MTA then searches the “Domain Name System” (DNS) for the IP address of the recipient’s mail server.
EXTERNAL FORWARD SERVER
If the recipient’s domain is connected to the same mail server as the sender, the e-mail is delivered directly. Otherwise, the MTA splits it into small data packets, which are forwarded to the destination SMTP server via the shortest path and which at the same time has less traffic. Packets sometimes pass through several MTAs on external SMTP servers (called “Relay” in technical jargon), which ensure continuous forwarding.
RECIPIENT’S INCOMING MAIL SERVER
Upon arrival at the destination SMTP server, the data packets are reassembled to form a complete e-mail. The MSA and / or MTA once again checks for spam and then transfers the e-mail to the message archive of the incoming mail server. From there, the so-called “Mail Delivery Agent” (MDA) transmits the message to the recipient’s mailbox. Then other IMAP or POP3 network protocols download the e-mail to the recipient’s SMTP client. Technically it would also be possible to send emails directly from the sender’s SMTP client to the recipient’s client. However, using an SMTP server offers a clear advantage: If the recipient’s incoming mail server is busy or temporarily out of service and the email cannot be delivered, the responsible SMTP server automatically attempts to deliver the email. e-mails at regular intervals. This happens until the delivery is successful or the mail is returned to the sender as undeliverable.
HOW DOES THE SMTP PROCEDURE WORK?
Understanding the SMTP procedure means understanding email. In practice it works like this:
- The SMTP client, or the sender, uploads the e-mail to the SMTP server, which is the outgoing mail server of the corresponding e-mail provider. This is done through a web application on the browser or through an e-mail program (technically called “Mail User Agent”, abbreviated MUA) such as Windows Live Mail or Mozilla Thunderbird.
- The SMTP server then contacts the DNS server, which searches for the IP address of the destination SMTP server (also known as “Mail Delivery Agent”, abbreviated to MDA) stored with the recipient’s e-mail address.
- The SMTP server sends the e-mail via one or more “Mail Transfer Agents” (MTA) to the destination SMTP server. Each of these forwarding processes occurs according to the SMTP protocol.
- The destination SMTP server saves the e-mail temporarily in the message archive.
- The MUA recipient downloads the email via IMAP or POP3.

DEEPENING
A mail is sent from a mail client (mail user agent, MUA) to a mail server (mail submisson agent, MSA), using SMTP over TCP on port 587. Most mail providers however still allow sending on the traditional port 25. The MSA delivers the mail to the mail transfer agent (MTA). Often MSA and MTA are instances of the same software, started with different options on the same machine. In addition to a classic client, an outgoing mail account with SMTP protocol can be configured in any software application that can send e-mail. The MTA uses DNS to find the MX record of a specific domain (the part of the address after the @ character). The MX record contains the name of the target host. Based on the host name and other information, the MTA chooses a server and connects as an SMTP client. Message transfer can occur in a single connection between two MTAs or through a series of hops across several intermediary systems. An SMTP server can be the recipient of the message or intermediary (performing store and forward operations) or gateway (it can transmit the message using other protocols as well as SMTP). Each jump is a formal transfer of responsibility over the message, so each server receiving the message must deliver it or report an error. Once the receiving server accepts the incoming message, it delivers it to a mail delivery agent (MDA), who saves it in a mailbox for local delivery. Once delivered to the mail server, the message is stored for retrieval by a specific authenticated mail client (MUA). The e-mail is retrieved through applications on the user’s device, called mail clients, using the Internet Message Access Protocol (IMAP), which facilitates both access to the e-mails and manages the stored e-mails, or Post Office Protocol (POP) which typically use the traditional mbox format for emails, or a proprietary system such as Microsoft Exchange / Outlook or Lotus Notes / Domino. Webmail clients can use both ways but the retrieval protocol is usually not a standard protocol. POP3 and IMAP are similar protocols but with some substantial differences: POP3: the mail client connects to the server, downloads the mail locally, deletes the messages downloaded from the server and disconnects (it is however possible to set some parameters to avoid deleting the email from the server). Characteristics of this protocol: possibility of having messages always saved locally, therefore an internet connection is not necessary (obviously necessary for sending and downloading new messages) and saving space on the server. IMAP: the mail client connects to the server, requests new messages and presents them to the user by saving them in the form of temporary files (similar to POP3, it is possible to save the mails locally permanently). Any changes you make to messages are also reflected on the server and any other device you are logged in to. Features: mail saved on the server therefore always available from any device through authentication, possibility to retrieve the mail even if a specific device on which the mail is consulted stops working, saving space on the client. SMTP defines how the message is transmitted, not its content. It defines the structure and its parameters, such as the envelope sender, but not the header (except for the tracking information) or the body of the message itself. STD 10 and RFC 5321 define the structure of SMTP while STD 11 and RFC 5322 define the message (header and body) through an Internet Message Format.
STRUCTURE OF THE PROTOCOL
SMTP is a connection oriented, text based protocol, in which a mail sender communicates with a mail receiver by sending command strings and providing the necessary information through a reliable communication channel, typically based on TCP. An SMTP session consists of the exchange of commands generated by an SMTP client and the corresponding responses of the SMTP server. A session can include zero or more SMTP transactions. An SMTP transaction consists of three sequences of commands and responses:
MAIL FROM: command to define the return address, also called return-path, reverse-path, bounce address, mfrom or envelope sender.
RCPT TO: command to define the recipient of the message. This command can be sent multiple times, once for each recipient (the addresses are part of the structure (envelope)).
DATA: command sent to signal the beginning of the text message, the content of the message, as defined in the envelope. It consists of a header and a body, separated by a blank line. DATA, however, is a set of commands to which the server responds twice: the first time as a confirmation of receipt of the text (acknowledge), the second after the end-of-data sequence to accept or reject the entire message. In addition to the intermediate responses to the DATA command, each server response can be positive (characterized by the code 2xx) or negative. Negative responses can be permanent (5xx) or temporary (4xx). A reject represents a permanent failure and the client should send a bounce message to the server from which it received the message. A drop is a positive response, followed by the rejection message, rather than the delivery message. The initial host, the SMTP client, can either be a user’s mail client, referred to as a mail user agent (MUA) or rely on a mail transfer agent (MTA), which is in fact an SMTP server that behaves like an SMTP client for the current session. More advanced SMTP servers maintain a message queue to resend messages that have failed (temporary) delivery. A relay server typically determines which server it should connect to through each domain’s DNS MX (Mail eXchange) record. If no MX record exists, some servers check the A record. The main difference between MTA and MSA is that connecting to an MSA requires SMTP authentication. The division between MTA and MSA has several benefits: The MSA, since it interacts directly with the user (through the MUA), can correct small errors in the message format (for example, missing date, missing recipient, non-existent domain name etc. ). An MTA accepting a message cannot reliably and securely make these changes as any changes made by the MTA reach the sender of the message after the message has already been sent. MSA and MTA may have different spam blocking solutions. Most MSAs require email and password authentication and therefore the sender of the message can be traced. This allows the MSA to have a less stringent spam policy.


MESSAGE RETRIEVAL
SMTP is a delivery protocol only. In the most common use, the message is sent to the destination mail server, or to the server in the next step. The message is routed based on the destination server, not based on the user to whom it is to be sent. Other protocols such as Post Office Protocol (POP) and Internet Message Access Protocol (IMAP) are specifically developed to be used by the user, retrieving messages and managing the mailbox. To allow an intermittently connected mail server to retrieve messages from a remote server, SMTP has a function to initiate a message processing queue on a remote server. Remote Message Queue Initialization is a SMTP feature that allows a remote host to initiate processing of the mail queue on a server, which can receive messages intended for it by sending a TURN command. However, this feature was deemed insecure and was replaced (RFC 1985) by the ETRN command which operates more securely using an authentication method based on Domain Name System Information.
SMTP SERVER
An e-mail client needs to know the IP address of the starting SMTP server, which must be provided as part of its configuration (usually as a DNS name, MX field). Under these systems, an ISP does not allow access to the SMTP server by users outside the network managed by the ISP itself. More precisely, the server could only allow access by users with an IP address provided by the ISP, which is equivalent to requiring both, sender and recipient, to be connected to the internet using the same ISP. A mobile user, however, may often be on a network that is not that of his normal ISP and therefore may not be able to send mail because the configuration of the chosen SMTP server is no longer accessible. An organization’s SMTP server could therefore only provide services to users on the same network, blocking access to the external network. Alternatively the server could perform a range check on the client’s IP address. These methods were typically used by entities and institutions such as universities that provide an SMTP server for internal organization use only. However, many of these organizations now use an authentication method. When a user is mobile, and could connect to the internet through different ISPs, this type of usage restriction is onerous and changing the address of the exit server is impractical. It is desirable to be able to use mail client configurations that do not need to be changed.
CLIENT AUTENTICATION
Modern SMTP servers usually require client authentication through credentials, before allowing access, instead of directly blocking access based on location, as described above. This more flexible system allows mobile users to have a fixed outboud SMTP server. SMTP authentication, often abbreviated as SMTP AUTH, is an extension of SMTP to allow access through authentication mechanisms. Communication between mail servers usually takes place through TCP on port 25, although email clients usually use another port. Mail services usually accept mail sending on ports: 587 (delivery), as standardized in RFC 6409 (formerly RFC 2476). 465. This port was deprecated by RFC 2487, after being assigned to the secure SMTP service in 1990. Nevertheless, it is commonly used by mail providers. Port 2525 and others may be used by some providers but are not officially supported. Many Internet Service Providers now block all mail sent from port 25, as an anti spam measure, and only allow it to be sent from the designated mail server. The provider can thus control the outgoing traffic.
SMTP COMMAND
HELO: Sent by a client for self-identification, usually with a domain name.
EHLO: Allows the server to identify support for Extended Simple Mail Transfer Protocol (ESMTP) commands.
MAIL FROM: Identifies the sender of the message. Used in the form MAIL FROM :.
RCPT TO: Identifies the recipients of the message. Used in the form RCPT TO :.
TURN: Allows the client and server to switch roles and send mail in the opposite direction without having to establish a new connection.
ATRN: The ATRN (Authenticated TURN) command uses, at its discretion, one or more domains as a parameter. The ATRN command must be rejected if the session has not been authenticated.
SIZE: Provides a mechanism by which the SMTP server can indicate the maximum supported message size. Compatible servers must provide size extensions to indicate the maximum allowable message size. Clients should not send messages larger than the size indicated by the server.
ETRN: An extension of SMTP. ETRN is sent by an SMTP server to request that another server send any e-mail messages it has.
PIPELINING: Allows you to send a stream of commands without waiting for a response after each command.
CHUNKING: It is an ESMTP command that replaces the DATA command. This command sends a BDAT command with an argument containing the total number of bytes of the message so that the SMTP host does not have to continually scan to determine the end of the data. The receiving server counts the bytes in the message, and when the message size matches the value sent by the BDAT command, the server assumes that it has received all of the message data.
DATA: Sent by a client to initiate the transfer of the contents of a message.
DSN: This is an ESMTP command that triggers delivery status notifications.
RSET: Cancel the entire message transaction and reset the buffer.
VRFY: Verify that a mailbox is available for message delivery. For example, VRFY ted verifies that Ted’s mailbox resides on the local server.
HELP: Returns the list of commands supported by the SMTP service.
QUIT: End the session.
SMTP COMMUNICATION EXAMPLE
Below is an SMTP transaction between two mailboxes (Alice and Bob) that are on the same domain (example.com). The lines sent by the client are preceded by “C:”, while those sent by the server by “S:” (however these letters are not part of the message exchange but serve only as an example).
S: 220 smtp.example.com ESMTP Postfix
C: HELO relay.example.com
S: 250 smtp.example.com
C: MAIL FROM: <bob@example.com>
S: 250 OK
C: RCPT TO: <alice@example.com>
S: 250 OK
C: DATA
S: 354 End data with .
C: From: “Bob” <bob@example.com>
C: To: “Alice” <alice@example.com>
C: Date: Tue, 15 January 2008 16:02:43 -0500
C: Subject: Test message
C:
C: Hi, this is a test message
C: .
S: 250 Ok: queued as 12345
C: QUIT
S: 221 Bye
The client notifies the recipient of the mail through the RCPT TO command. In the event that the message cannot be delivered, a bounce address is returned. In this case the message is sent to a mailbox on the same server (if there was also a Cc, the message would also be sent to his mailbox). The corresponding SMTP command is RCPT TO. Each command executed successfully leads to the generation of an acknowledge by the server with code 250. The beginning of the transmission of the mail text is identified by the DATA command, after which the text is transmitted line by line and ends with the sequence. called the end-of-data sequence. Since a line can only contain a period (.) As part of the text, the client sends two consecutive points whenever a line begins with a period. Similarly, the server replaces each sequence of consecutive colons with just one (this technique is called dot-stuffing). The server’s positive response to the end-of-data means that the server has taken over the delivery of the message. A message can be duplicated if, at this stage, a communication problem occurs, caused for example by a power failure. Until the sender receives the message with code 250, it is assumed that the message has not been delivered. Similarly, after the recipient decides to accept the message, the sender assumes that the message has been delivered. However, during this time frame (time between when the message is sent to when the client receives the response characterized by code 250), both agents have active copies of messages that they try to deliver and this can cause message problems. duplicates. To limit this phenomenon, a timeout time of between 5 and 10 minutes is usually specified. The QUIT command ends the session. If the mail has other recipients, the client will connect to an appropriate SMTP server for subsequent recipients. The information that the client sends with the HELO and MAIL FROM commands are inserted (not shown in the example code) in the mail as additional header fields, by the recipient server, adding the Received and Return-Path fields respectively. Some clients are implemented in such a way as to close the connection after the message has been accepted (in the example 250 OK: queued as 12345), so the last two lines can be omitted. However, this solution can cause the server to fail when sending the 221 response.
THE SECURITY OF THE SMTP PROTOCOL
One of the limitations of the original SMTP protocol is that it does not handle authentication of senders. In addition to the risk of spam, there is the possibility of sending e-mails by making the address corresponding to another account appear as the sender. Without accessing the third party account, it is possible to establish a connection to the mail server and write a message in SMTP code containing the commands relating to sender and recipient, to give the relative parameters and the body of the e-mail. To overcome these problems, an extension called SMTP-AUTH has been developed. Despite this, spam remains a major e-mail problem to this day. However, a radical revision of the SMTP protocol is not considered feasible, due to the large number of implementations of the current protocol (for example, Internet Mail 2000 has been proposed as an alternative protocol). For this reason, several auxiliary protocols have been proposed to assist SMTP transactions. The IETF Anti-Spam Research Group is working on various email authentication proposals centered on flexibility, lightness and scalability.
MIME
MIME (Multipurpose Internet Mail Extension) allows you to compose emails containing special characters and attachments in binary format (photos, videos, etc). Some fields are added to the message header to signal the presence of MIME content so as not to “send mail programs into crisis”:
- MIME-version: for specification compliance.
- Content-Type: Describes the data in the message body to be interpreted by the recipient’s MUA.
- Content-Transfer-Encoding: Type of encoding used.
- Content-ID: to uniquely identify each MIME.
- Content-Description: textual description of the object (optional) A boundary string is defined: sequence of characters that delimits the beginning and end of a region.
POST OFFICE PROTOCOL
The Post Office Protocol (also called POP) is a Client-Server type application layer protocol which has the task of allowing, through authentication, access by the client to an e-mail account on a host server and download the e-mails of the account itself. The protocol for sending mail is the SMTP protocol.
DESCRIPTION
The Post Office Protocol (POP3) allows the retrieval of e-mails with the help of a client. For this purpose, the client establishes a connection with the incoming mail server, on which the necessary POP3 server software must be installed. Emails located on this server are downloaded and stored on the computer client. At the same time, the electronic messages are deleted from the mail server and the connection is interrupted. You can open and edit email content locally only, without the client and server being connected. The length of the retrieval process varies based on the size of the email and attachments. Messages can only be downloaded from a POP3 client. In the process of connecting to the mail server via TCP / IP protocol, POP3 clients use port 110. If the connection is encrypted, port 995 is used. If server and client are connected, they communicate via commands. POP3 commands consist of three or four characters and one or more parameters. The server responds to each command with a positive (+ OK) or negative (-ERR) status signal and optional information. Each POP3 session is divided into 3 phases: the first step is user access, in which the client identifies himself to the mail server with a username and password. Then follows the actual process of retrieving the messages. If all emails have been downloaded and the client disconnected, they are deleted from the server at a later time. If a connection break occurs during the recovery phase, all e-mail messages remain on the server, so that the POP3 client can download them again with the next connection.
INTERNET MESSAGE ACCESS PROTOCOL
IMAP (short for Internet Message Access Protocol) is a text-based network protocol that makes it possible to access e-mails located on a mail server. If you configure your account via IMAP, your client establishes a connection with the server at each login, which remains active throughout the session: during this time you have access to individual folders and e-mails, the contents of which are displayed on request. All messages and folders created remain stored on the server until they are deleted. However, you can access your mail from anywhere. The connection between IMAP server and client is established through the TCP / IP protocol on port 143 (with port for secure connection 993). The client then communicates with the mail server via text messages, but does not need any response to the commands issued. In order for it to subsequently record the server response, the client includes an identifier in its commands, which adds the responses to the mail server. If their content has information, the answers start with an asterisk. If there is a plus symbol before the response, the server expects other information in addition to the command already received. Furthermore, the response informs about the success (OK) or failure (NO) as well as syntax errors (BAD) of the respective commands issued by the IMAP client.
DIFFERENCES BETWEEN IMAP AND POP
A comparison between the two protocols shows that there are some differences between IMAP and POP3: while clients using IMAP establish a permanent connection with the mail server, the connection of the client and POP3 server is established only during the recovery phase messages. This is closely related to the different treatment in email retrieval. Using the POP3 protocol, the downloaded e-mails are deleted from the server, on the contrary, if you use the services of the IMAP network protocol, all messages remain on the server until they are manually deleted. This is also the reason why, with the use of the IMAP protocol, multiple clients can have access to the same data collection at the same time. With POP3, access is limited to a single client, as all e-mails are always downloaded to the local computer.
IMAP FOR MORE CLIENTS, POP3 FOR ONE
The differences highlighted between IMAP and POP3 also correspond to different possibilities of use: since POP3 is limited to only one client and all e-mails are always completely recovered, the use of this transmission protocol is worthwhile, if you want to recall your account and -mail from a local computer. If e-mails are downloaded once, you do not need any further connections to the mail server and can therefore read and edit your e-mails even without an internet connection. If, on the other hand, you want to access the same e-mail with a smartphone, tablet or multiple clients, IMAP is the best solution. In particular, if while you are out and about you can only take advantage of the data connection of mobile devices, it is an advantage that IMAP only calls up the desired e-mails. This way you can open messages with large content from your home PC. Since no local version of the e-mails are downloaded, an existing internet connection is required in any case. Using the function to retrieve e-mails with the IMAP network protocol, you can also create and manage folders, mark the processing status of e-mails and archive sent messages. Thanks to these additional functions and the fact that e-mails are stored on the server until they are deleted, IMAP uses the mail server more than POP3. The choice between IMAP or POP3 should depend on both the intended use and the resources available.
DEEPENING AI
Simple Mail Transfer Protocol (SMTP) is the standard protocol for sending emails over the Internet. First defined in 1982 with the publication of RFC 821 (later updated by RFC 5321), it is one of the fundamental protocols that supports the electronic communications infrastructure.
1. Function and Role of SMTP
SMTP is primarily used to transfer email messages from a sender to an email server (Mail Transfer Agent, MTA) and between email servers themselves. Its primary goal is to ensure the correct transmission of the message and recipient information to the recipient’s mail server.
2. SMTP Architecture
SMTP architecture is based on client-server communication. Here is an in-depth look at the main components:
•SMTP Client: This is the system that initiates the transmission of the email message. This could be a MUA (Mail User Agent), i.e. a mail client such as Outlook or Thunderbird, or an MTA that transfers emails from one server to another.
•SMTP Server: This is the entity that receives the message from the client. It can act as the final recipient or forward the message to other servers to reach the correct destination.
In a typical sending cycle, the sender sends the email to its SMTP server, which passes it on to the recipient’s SMTP server, using a series of steps called store-and-forward.
3. How It Works
SMTP can be described as a sequence of commands and responses between the SMTP client and the SMTP server. Here is a simplified process for sending an email:
1. Connection: The SMTP client establishes a TCP connection to the SMTP server, usually on port 25 (although ports 587 or 465 are also common today, for secure connections).
2. Initial Handshake: Once the connection is established, the server sends a welcome message. The client responds by sending the HELO or EHLO command to start the conversation. Using EHLO indicates that the SMTP client supports SMTP extensions, such as secure transmission (STARTTLS).
3. Sending the sender and recipient: The client sends the MAIL FROM command to specify the sender’s address and RCPT TO to specify the recipient of the email. The server responds to each of these commands with a confirmation message, indicating whether the recipient is accepted or if there are problems.
4. Sending the message: Once the server has accepted the recipient, the client sends the DATA command followed by the message content (including the message body and headers). The sending ends with a period (.) on a new line. The SMTP server responds with a status code indicating whether the message was accepted.
5. Closing the connection: After sending the message, the SMTP client sends the QUIT command to close the connection.
4. SMTP Status Codes
SMTP uses a series of 3-digit response codes that indicate the status of each operation. Some of the most common codes include:
•2xx: Success. For example, 250 means that the requested action was completed successfully.
•4xx: Temporary error. For example, 421 means that the service is unavailable.
•5xx: Permanent error. For example, 550 means that the recipient’s email address is unavailable or does not exist.
5. Security in SMTP
SMTP, in its original form, does not provide encryption or authentication, which makes it vulnerable to attacks such as “Man-in-the-Middle” or interception of the content of the message. However, over time, various mechanisms have been introduced to improve the security of the protocol:
•STARTTLS: An extension that allows you to upgrade an insecure SMTP connection to an encrypted connection using TLS (Transport Layer Security).
•SMTP-AUTH: Provides a mechanism to authenticate the sender during message transmission, preventing emails from unauthorized senders.
•DKIM, SPF and DMARC: These mechanisms help prevent email address spoofing, improve message integrity verification and reduce spam.
6. Protocol Extensions
The SMTP protocol has been extended over time with numerous additional features. Some of the most common include:
•ESMTP (Extended SMTP): Introduced with RFC 1869, ESMTP adds extensions to SMTP, such as authentication, server capacity management and support for secure transmission.
•8BITMIME: Allows the transfer of emails with 8-bit content, instead of the traditional 7-bit ASCII, improving support for non-Latin characters.
• SMTPUTF8: Extension that allows the use of Unicode characters in email addresses and message content.
7. Limitations and Problems of SMTP
Despite its robustness, SMTP has some limitations:
•Lack of native encryption: The original protocol does not include cryptographic protections. Although STARTTLS is a common solution, not all servers support it.
•Dependence on incorrect configuration: A malfunctioning or misconfigured SMTP server can lead to lost, bounced or mishandled emails.
•Spam: SMTP, without adequate security measures such as authentication and the use of DMARC, SPF and DKIM, is vulnerable to abuse by spammers.
8. Use in Modern Environments
SMTP is still the dominant protocol for transmitting emails, although it is combined with other protocols such as IMAP (Internet Message Access Protocol) or POP3 (Post Office Protocol) for receiving emails. While SMTP is used to transfer emails from server to server, IMAP and POP3 are used to retrieve emails from the recipient’s mail server to the client.
In short, SMTP is an essential protocol that has stood the test of time, ensuring email transmission over the Internet for decades. Through continual improvements and extensions, it remains at the heart of electronic communication, even in an era of growing concern for security and privacy.



Leave A Comment