HOSTNAME AND IP ADDRESSES


LOCAL TRANSLATION
You can enter IP associations: Name manually in the hosts.txt (Windows) and /etc/hosts (Linux and MacOS) files:
THE DNS
In computer science and telecommunications, the Domain Name System is a system used to assign names to network nodes (in English: hosts). These names can be used, by means of a translation, usually called “resolution”, in place of the original IP addresses. The service is implemented through a distributed database, consisting of DNS servers. DNS has an inverted tree hierarchical structure and is divided into domains (com, org, it, etc.). Each domain or node corresponds to a nameserver, which keeps a database with the information of some domains for which it is responsible and turns to subsequent nodes when it needs to find information belonging to other domains. Each domain name ends with a “.” (point). For example, the wikipedia.org address ends with a period. The string following the trailing dot is called the DNS root zone. The servers responsible for the root domain are the so-called root nameservers. They own the list of authoritative servers of all recognized top level domains (TLD) and provide it in response to each request. There are 13 root nameservers worldwide, including 10 in the United States, two in Europe (England and Sweden) and one in Japan. The DNS name also denotes the protocol that governs the operation of the service, the programs that implement it, the servers on which these are processed, the set of these servers that cooperate to provide the most intelligent service. DNS names, or “domain names” or “mnemonic addresses”, are one of the most visible features of the Internet. The conversion operation from name to IP address is called “DNS resolution“; the conversion from IP address to name is called “reverse resolution“. In practice, the DNS is a universal registry that is a distributed database, with a hierarchical structure, which stores the mnemonic domain names and their association with their specific IP addresses.
REASONS AND USES
The ability to give a textual name that is easy to memorize to a server (for example a world wide web site) greatly improves the use of the service, as humans find it easier to remember textual names (while hosts and routers are reachable using numeric IP addresses). For this reason, the DNS is fundamental for the widespread diffusion of the internet even among non-technical users, and is one of its most visible characteristics. It is possible to assign multiple names to the same IP address (or vice versa) to represent different services or functions provided by the same host (or multiple hosts providing the same service). This “flexibility” is useful in many cases:
- In the event that the server hosting a service needs to be replaced, or its IP address needs to be changed, simply change the DNS record, without having to intervene on the clients.
- By using different names to refer to the different services provided by the same host (therefore registered with the same IP address), it is possible to move a part of the services to another host (with a different IP address, already set up to provide the services in question). Therefore, by modifying the name records associated with the services to be moved on the DNS server and registering the new IP in place of the old one, the new requests of all clients will be automatically moved to this new host, without interrupting the services.
- A very popular use of this possibility is the so-called virtual hosting, based on names, a technique whereby a web server with a single network interface and a single IP address can host multiple websites, using the alphanumeric address transmitted in the HTTP header to identify the site for which the request is made. By matching a name to multiple IP addresses, the load of the clients requesting that name is spread across the different servers associated with the registered IPs, resulting in an increase in overall service performance and fault tolerance (but you need to make sure that the different servers are always aligned, i.e. they offer exactly the same service to clients). Reverse resolution is useful for identifying the identity of a host, or for reading the result of a traceroute. DNS is used by numerous technologies in a way that is not very visible to users, to organize the information necessary for the functioning of the service.
DOMAIN NAMES
A domain name consists of a series of strings separated by periods, such as it.wikipedia.org. and are organized in levels. Unlike IP addresses, where the most important part of the number is the first digit starting from the left, in a DNS name the most important part is the first starting from the right. The rightmost part is called the Top Level Domain (or TLD), and there are hundreds of them that can be chosen, for example .org, .it, .com etc. A second level domain, unlike the top level domain which is made up of “fixed” and limited words, is made up of a word chosen at will. This word must be linked as much as possible to what identifies us and what we want to communicate. The second level domain is therefore formed by two parts, for example wikipedia.org, and so on. The third level domain is the child of the second level domain, in fact, taking wikipedia.org as an example, a third level domain will be: stuff.wikipedia.org. Each further element therefore specifies a further subdivision. When a second level domain is registered to the assignee, the assignee is authorized to use the domain names related to the following levels, such as some.other.stuff.wikipedia.org (fifth level domain) and so on.
HIERARCHICAL ORGANIZATION OF NAMES
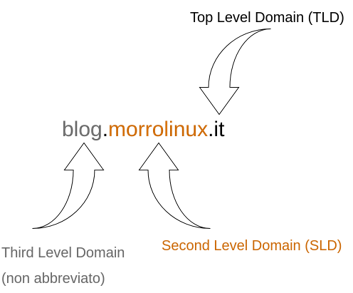
The SLD (Second Level Domain) can have the name of our business, organization, initiative or project. Getting a third level domain is not really a problem if we have bought a second level domain, because it is at a “lower” level of the hierarchy.
TLD and SLD form a tree:

They are made up of names such as “test.lab.morrolinux.it“, “mail.google.com” etc. The Top Level Domains are also logically grouped by a higher node, called “root”.
NB: the address resolution occurs from the highest to the lowest point of the hierarchy.
NS (NAMESERVER)
A nameserver has the purpose of, given a hostname, resolve its IP address or indicate another nameserver under its hierarchy that can do so.
There are several types of NS:
Root Nameserver (.)
is the root of the domain tree, it knows the NameServer TLD
TLD Nameserver (.com, .it, .fr etc.)
for example, the “it” TLD will know the SLD nameservers of all the Italian sites
SLD Nameserver
for example morrolinux.it, will know all the hosts under it.
TYPES OF RECORDS
Different types of information can correspond to a DNS name. For this reason, there are several types of DNS records. Each DNS database entry must have a type. The main types are:
- Record A – Indicates the correspondence between a name and one (or more) IPv4 addresses.
- MX record – (Mail eXchange) indicates to which servers e-mail should be sent for a certain domain.
- CNAME records – They are used to create an alias, that is, to make sure that the same host is known by multiple names. One of the uses of this type of record is to give a host that offers multiple services a name for each service. In this way, the services can then be moved to other hosts without having to reconfigure the clients, but only by changing the DNS.
- PTR record – DNS is also used to perform reverse resolution, i.e. to match the corresponding domain name to an IP address. For this we use the records of type “PTR” (and a special area of the namespace in-addr.arpa).
- AAAA Record – This is like Record A but works with IPv6 and returns an IPv6 address.
- SRV Records – Identify the server for a particular service within a domain. They can be considered a generalization of MX records.
- TXT records – Associate arbitrary text fields with a domain. These fields can contain an informative description or be used to create services.
There are also types of “service” records, which are necessary for the distributed database to function:
- NS Record – Used to indicate which DNS servers are authoritative for a certain domain, or to delegate their management.
- SOA Record – (Start of Authority) used for managing DNS zones.
In the DNS can be entered other types of records, some folkloric, such as “LOC”, used (little) to report the geographical coordinates of a site, others add security functions to avoid tampering. DNS implements a hierarchical namespace, to allow parts of a namespace, known as “zones”, to be delegated from one name server to another name server further down the hierarchy.
NAME RESOLUTION SCHEME

TIME TO LIVE
The records associated with a domain name can change over time, allowing for example to assign a new IP address to a server, making it continue to respond to the name already known to users. Each DNS record has an associated parameter called time to live or TTL (time to live), which indicates how long this record can be stored in a DNS cache system before it is considered expired. When a server responds to a request with a record taken from its cache, it assigns the record’s remaining time to live to the response. So if the record originally has a TTL of 12 hours, and a server responds to a request with data it got two hours ago, it will put a 10 hour TTL in the response.
ZONES, DELEGATES AND REPLICAS
A DNS “zone” is a part of the namespace, consisting of a domain and its subdomains which are not themselves delegated, which is under the same administrative management and therefore is managed by one or more servers. The management of a zone is “delegated” by the upper zone through NS type records. For example, in the .org zone there will be a delegation for the wikipedia.org zone to the DNS servers that manage it. For redundancy reasons, each zone is “replicated” on multiple servers, and consequently the delegation consists of multiple NS records, which indicate that each of the servers indicated contains the information for that zone (ie it is “authoritative” for the zone) . Within a zone, lower level zones can be delegated, for example in wikipedia.org there may be proxies for devel.wikipedia.org or for accounting.admin.wikipedia.org. Each domain, therefore, has an authoritative DNS server. The different servers that are delegated for a zone should contain the same information, so that any one of them can answer a query for a record in the zone. The replication scheme typically has a master (primary) server, which is the one on which information is updated, and one or more slave (secondary) servers, which copy information from the master when needed. To keep track of the different “versions” of a zone that may be in circulation, and in particular to allow a secondary to decide whether to transfer the zone from the primary, each zone has a serial number, which must be increased each time changes are made on the primary. To obtain the serial number of a zone present on a server, an SOA query is performed. The secondary compares its serial number with that of the primary, and if that of the primary is higher, it transfers the zone. The operation of copying all the records of a zone from the master to a slave is called zone transfer, and can be complete (all the contents of the zone are copied) or incremental (only the records modified with respect to the version already present are copied) . Some DNS implementations allow you to change zones from any authoritative server, propagating the changes to other servers. The root (root) of the DNS name tree is the zone. (period), which is managed by a set of servers called root servers.
HOW TO UPDATE THE DNS SYSTEM
Root Nameserver
Each Root NS receives an updated copy of the “root zone” file from Verisign each week, containing any new TLD names that have been registered.
TLD e SLD Nameserver
Each new NS must register with the NS of the upper zone to “officially exist”.
AUTHORITATIVE NS
To manage a domain, you need an authoritative nameserver for that domain.
- It is registered with the hierarchically superior domain;
- It knows all the IP addresses of the hostnames of that domain.

The authoritative nameserver is called master and is configured by the network administrator with the “master file” which contains the associations between names and IP addresses. The DNS specification requires that there is at least one secondary (slave) authoritative server that keeps a copy of the master file updated to guarantee service in case of failures. Updates to IP: Name associations are made in the master NS master file, and the slave servers will periodically check for updates to download.
DNS ZONES
The primary (master) Name Server does not necessarily have to know all the IP addresses of the domain, because it can delegate the management of a part of the namespace (i.e. a zone) to another server.

In this case Zone and Domain do not coincide, because we have created two zones. In doing so we will therefore have to have two primary NS, one responsible for each area.

ITERATION AND RECURSION
In general, to obtain the resolution of a name it is necessary to start from the root, query one of the root servers in the top-level domain, obtain the server that manages it, query it in the second-level domain, until reaching the authoritative server for the name desired. This technique is called “iteration“. Recursion instead delegates the various queries to the servers themselves: a request is made to the root server, which itself forwards it to the TLD server, which forwards it to the authoritative server and so on until the desired server is reached. The DNS response proceeds in reverse until it reaches the client that made the request.

CACHING
Some servers lend themselves to performing recursive queries on behalf of some clients. Once they get an answer, they cache all the information they have learned until it expires. Some implementations of the DNS service allow the creation of so-called caching only servers, ie without their own database, but useful for redirecting resolution queries to an authoritative server. This feature is especially useful when resolution must be done through slow links (with speeds below 500 kbps) or firewalls.
DNS PACKAGES

(*) Errata corrige: rcode non zcode.
DNS is an Application level service. A DNS packet is then encapsulated in a Transport (UDP) layer packet, which in turn will be encapsulated in a Networking (IP) layer packet and so on. By default, DNS requests / responses are on UDP protocol, so the Transport layer packet will be a UDP packet. A DNS packet can represent a request (query) or an answer (answer) from the server.
The most important fields:
- Query ID: allows the server to associate a request / response from a certain client.
QR (Query / Response): it is 0 if it is a request, 1 if it is a response; - AA (Authoritative Answer): it is 1 from the server if the answer is authoritative, 0 otherwise;
- TC (Truncated): Set to 1 by the server if the response falls outside the 512-byte limit of a single UDP packet;
- RD (Recursion Desired): Set to 1 if the client would like a recursive request;
- RA (Recursion Available): The server communicates whether it supports (1) or not (0) recursive requests;
- rcode: is the response code of the server, and indicates success or failure.
- Question count, Answer count, etc. they are counters (we will see later in the example).
Example:
DNS request package for the A record blog.morrolinux.it:
qr = 0 (it is a request);
Opcode = 0 (this is a normal query)
rd = 1 (recursion is desired);
Question count = 1 (one question)

Received DNS Response Packet:
qr = 1 (answer);
AA = 0 (non-authoritative);
ra = 0 (recursion not available);
rc = ok
⇒ Question count = 1 (the question in the answer packet is repeated),
⇒ Answer count = 0 (the answer given is not related to the question),
⇒ Authority count = 2 (two authority records are returned),
⇒ and 2 additional records (Additional record count):
More precisely, the DNS server in question has returned the authoritative Name Server for the “morrolinux.it” domain and its secondary one. These two name servers are ns1.morrolinux.it and ns2.morrolinux.it, but we cannot know what IP they have to contact them!
⇒ In the two additional records we are given the relative IP addresses for ns1 and ns2.
⇒ We can go on, sending a DNS request this time to ns1 or ns2, and getting the final answer.

USE
To use the service, one or more referral DNS servers must be configured on each client. These are designed to perform recursive queries and perform caching services. When a system needs to communicate with another system, it asks the referring DNS server to carry out the process called “resolution” of the name in an IP address. The server searches its database to obtain the IP address corresponding to the searched system. If the queried server has the requested information, the search process ends by sending the IP address to the requester. If the search fails, the server makes a “recursive” request.
ROOT NAMESERVER
Within the Internet, a root nameserver is a DNS server that responds to name resolution requests regarding the main domain namespace (called root). Its task is to redirect requests for each top-level domain (TLD) to that TLD’s own nameservers.
Resolution mechanism in the root namespace
When a computer requests the DNS system to resolve a domain name, i.e. the conversion of a symbolic name into the corresponding IP address, the domain name is analyzed from right to left, asking each nameserver to provide information only on the element that is to the left of the last point. It should therefore be noted that all existing domain names on the Internet actually end with a. (period): strictly speaking, therefore, Wikipedia belongs to the domain “wikipedia.org.” (proof) The final point is implied; modern DNS management software does not require it to be explicitly specified to resolve the domain name. The empty string following the final dot is called the DNS root zone; all the top-level domains, both the individual ones of the single countries (.us, .uk, .it etc.) and the non-geographic suffixes (.com, .org, .net etc.), belong to this domain. The root nameservers are the servers responsible (in English “authoritative servers”, ie authoritative servers, with authority) for the domain “.”; in fact, they possess the list of servers responsible for each of the recognized top level domains, and provide it in response to each request. Each top-level domain (eg .org) has in turn a group of servers defined as authoritative, which in turn delegate a part of authority to the nameservers responsible for each second-level domain (eg wikipedia.org). The latter respond to queries on IP addresses relating to subdomains or individual hosts (eg www.wikipedia.org). Even if the domain names are often at three levels, nothing prevents you from having hosts corresponding to second level names (wikipedia.org) or to higher levels (www.italia.gov.it): the request always occurs in the same way. , by recursively querying the various nameservers. Furthermore, from February 4, 2008, the introduction of the first IPv6 addresses in the name resolution system began.
UTILITY AND LOAD OF NAMESERVER ROOTS
Currently, all queries to the DNS system on the Internet require the existence of root nameservers, so they are a critical element of the infrastructure. Not only does the accessibility of websites depend on them but also, through MX records, the routing of e-mails. The importance of the functioning of the nameservers is such that they have been subject to denial of service attacks by some viruses. For these reasons and to lighten the workload there are several, located in various places and under the authority of various organizations: however, this distribution has been the subject of controversy due to the centrality that the United States of America still has, and in in particular, the governmental institutions of the country, in the management of a critical infrastructure for the entire global Internet. In practice, most of the information provided by root nameservers does not change very often, and is stored in various caches by a hierarchy of DNS servers, which individual computers address before querying the primary nameservers; indeed, when a request for information is made, the response also contains information on how long it can be considered valid, precisely to make DNS resolution requests to root nameservers relatively rare. Unfortunately, there are a number of misconfigured systems on the Internet, which generate most of the traffic to root nameservers. For example, it happens that requests for resolution of names arrive at the main nameservers with the origin address set to 0.0.0.0 (corresponding to anywhere and in any place), and it happens that simple misconfigured desktop computers try to update the data contained in the nameservers main. For a list of curious cases in this regard, see the Bogus Queries article in the external links of this entry.
LIST OF NAMESERVER ROOTS
As of March 2007 there were 13 root nameserver names, of the form letter.root-servers.net, where letter can take the values from A to M. Some of them, already existing for some time, had another name before the convention was established current nomenclature. Currently it is not possible to add more server names, due to a protocol optimization problem: a UDP packet must be able to contain all server names and a 14th name would exceed the maximum packet size.

DEEPENING AI
DNS (Domain Name System) is a system for resolving domain names (such as www.example.com) into IP addresses (e.g., 192.0.2.1), which are necessary for devices to communicate with each other on networks such as the Internet. The following explains how DNS works at the application level, with a detailed description of the various steps and components involved.
1. What is DNS?
DNS is a protocol that operates at the application layer (layer 7 of the OSI model) and is used to translate human-readable domain names into machine-usable IP addresses. In fact, users prefer to remember and type domain names (such as google.com) rather than long, complex IP addresses (such as 142.250.181.206).
2. Main components of DNS.
-DNS Client (Resolver): When a user or application requests access to a domain, the DNS client (also called a “resolver”) initiates the request to find the IP address associated with that domain.
-DNS server: This is the computer that holds information about domain names and related IP addresses. There are several types of DNS servers:
-Local DNS server (resolver): Often configured by your ISP (Internet Service Provider), this is the first server contacted by the DNS client.
-authoritative DNS server: The server that is ultimately responsible for providing the correct response for a given domain. It includes root servers, TLD servers, and authoritative servers for specific domains.
3. Step-by-step operation of a DNS query.
1. Domain name entry: When a user enters a URL into a browser (e.g., www.example.com), the browser contacts the operating system to obtain the IP address associated with that domain.
2. Query to Local DNS Resolver: The operating system sends a DNS query to the local DNS server (also called a resolver). This server could be in the router, or it could be an ISP server or a public DNS server (such as those from Google or Cloudflare).
3. Resolver cache: The resolver checks to see if it already has the answer in its cache (a temporary memory that contains recent DNS results). If the requested IP address is already in the cache, the response is immediately returned to the client.
4. Query to DNS Roots: If the answer is not in the cache, the resolver begins the resolution process. It first sends a query to one of the 13 root DNS servers. The root servers do not know the exact domain address, but they provide the appropriate TLD (Top-Level Domain) server address (ex: for example.com, the TLD is .com).
5. Query to TLD Server: The resolver then sends a query to the TLD server that manages the top-level domain (e.g., the DNS server that manages all .com domains).
6. Query to the Authoritative DNS Server: The TLD server responds by indicating the authoritative DNS server for the requested domain (example.com), which contains the definitive information about the associated IP address.
7. Final Response: The resolver then sends a query to the authoritative server, which responds with the IP address associated with the requested domain. This information is then sent to the client (e.g., the browser), which can finally establish a connection with the server at the correct IP address.
8. Cache Storage: Before returning the response to the client, the local DNS resolver caches the IP address for a certain period (TTL – Time To Live), so that it can respond faster in case of future requests for the same domain.
4. Types of DNS Records.
When a DNS query is made, the response contains specific types of information, called DNS records. Some of the main records are:
-A (Address Record): Maps a domain name to an IPv4 address.
-AAA: Maps a domain name to an IPv6 address.
-CNAME (Canonical Name Record): Redirects from one domain name to another domain name.
-MX (Mail Exchange Record): Specifies the mail servers for that domain.
-TXT (Text Record): Contains textual information (used, for example, for authentication such as SPF and DKIM).
5. DNS and Security: DNSSEC.
DNS, born in the 1980s, was not designed with security in mind. DNS queries are not encrypted and can be vulnerable to various attacks, such as DNS spoofing or cache poisoning. To improve security, DNSSEC (Domain Name System Security Extensions) was developed, which adds cryptographic signatures to DNS records to ensure that responses come from an authentic source.
6. Recursive vs. Iterative DNS Requests.
-Recursive request: In this type of request, the DNS resolver makes all the queries necessary to resolve a domain name and returns the final response to the client. The user requests only one final response and does not bother with the process.
-Iterative query: The resolver returns to the client the address of another DNS server that may have the answer, and the client itself continues to send successive queries until it gets the final answer.
7. DNS Cache.
To improve performance and reduce the load on DNS servers, DNS results are cached both at the local resolver level and at the various intermediate DNS servers. Each DNS record has a TTL (Time to Live) value that specifies how long a response can be considered valid before it needs to be updated.
8. DNS over HTTPS (DoH) and DNS over TLS (DoT).
In response to privacy concerns related to unencrypted DNS queries, new protocols have been introduced to protect DNS requests:
-DoH (DNS over HTTPS): Sends encrypted DNS queries using the HTTPS protocol.
-DoT (DNS over TLS): Uses the TLS protocol to encrypt DNS queries.
These protocols improve privacy and security because they prevent third parties from intercepting DNS queries and monitoring visited sites.
9. Conclusion
DNS is a fundamental system for the operation of the Internet, as it allows domain names to be resolved into IP addresses, facilitating navigation and communication between devices. The process, although complex, is optimized for speed and efficiency through the use of caches and the hierarchical structure of DNS servers.



Leave A Comment